It is cybersecurity awareness month which is great timing for the Office of the Australian Information Commissioner (OAIC) have released their Notifiable Data Breaches (NDB) Report for 1 January to 30 June 2024 and it makes for an interesting read.
 The NDB scheme has reached it's sixth year of operation and has started to see stronger penalties for organisations and civil penalty
proceedings against company's such as Medibank
Private in
relation to its October 2022 data breach.
The NDB scheme has reached it's sixth year of operation and has started to see stronger penalties for organisations and civil penalty
proceedings against company's such as Medibank
Private in
relation to its October 2022 data breach.
From January to June 2024, OAIC received 527 data breach notifications. Cybersecurity incidents continue to be a prevalent cause of data breaches, representing 38% of the total.
With this, OAIC highlighted that as our increasing reliance on digital tools and online services exposes our details more frequently to malicious cyber actors. This serves as a reminder of how important it is that entities enact measures that guard against common threats, such as malicious actors using compromised credentials, ransomware and phishing, and update these measures as threats arise and change.
While 63% of data breaches affected 100 or fewer people, one incident reported affected over 10 million Australians. This is the second breach recorded to affect more than 10 million Australians and is the highest number of individuals affected by a breach since the NDB scheme came into effect.
Malicious or criminal attacks including cyber incidents top the list as the leading cause of data breaches involving personal information in Australia.
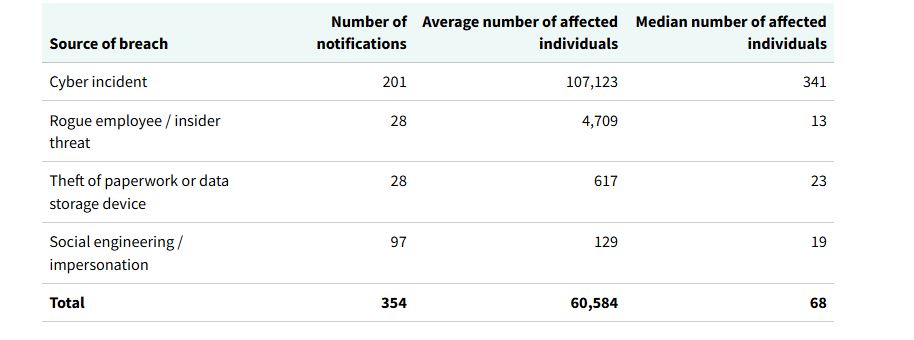
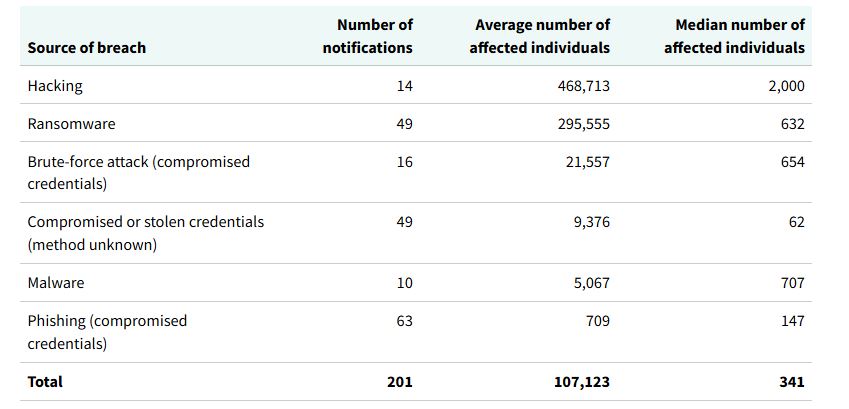
The report shows the number of data breaches caused by ransomware rose from 13 in the previous six-month period to 33 between January and
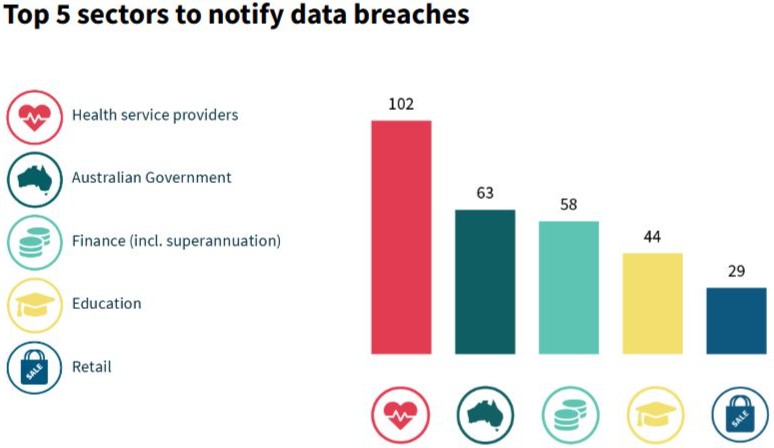
June. Here is a summary of the top sectors for breaches:
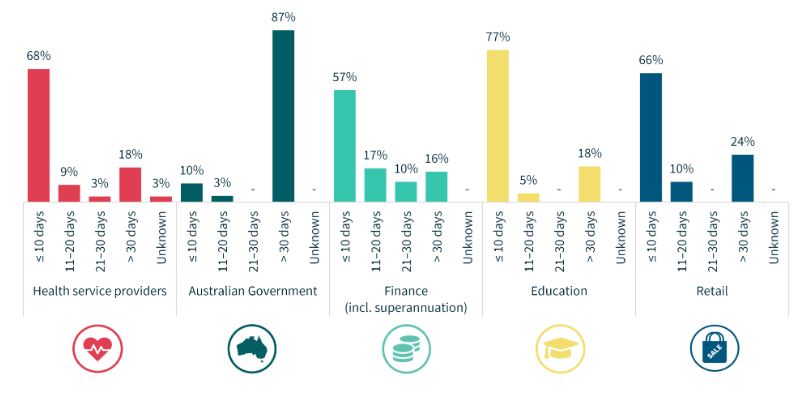
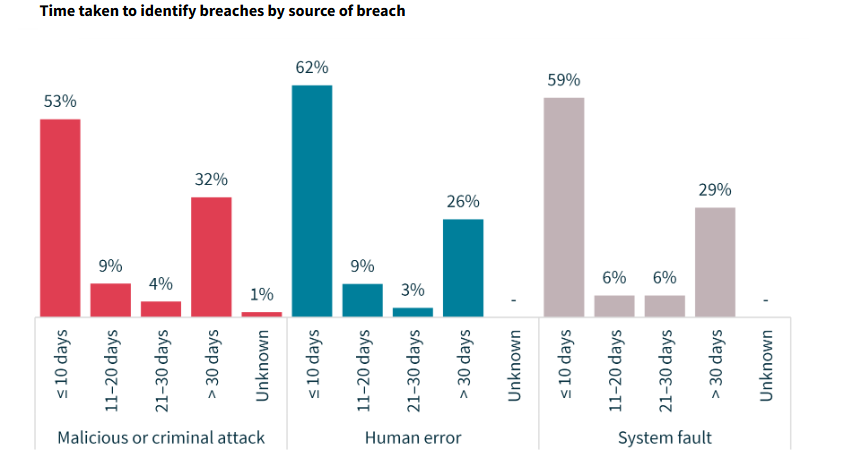
Approximately 69% of notifying entities were able to identify a breach within 30 days of it occurring, however, in 30% of instances the
entity took more than 30 days to become aware and assess that a data breach had occurred. A very sobering statistic when you think
about the amount of damage someone could do sitting in your network that long.
The number of notifications per month varied widely across the reporting period, ranging from 76 in January to 112 in May — perhaps coinciding with the lead up to end of financial year and an increase in ATO scams.
Cyber security incidents were the cause of 38% of all data breaches from January to June 2024.
In this reporting period, human error breaches accounted for 30% of all data breaches. Additionally, 31% of all breaches were caused by phishing,
where an employee inadvertently clicked on malicious links or downloaded a compromised attachment. Five per cent of all breaches were a
result of malware.


This is a timely reminder of how the human factor may pose a threat to the strength of an entity’s personal information security, regardless of how secure an entity’s systems are. Individuals may contribute to the risk of data breaches, intentionally or inadvertently.
Check out this real life example demonstrating how human error can result in a cyber security breach:
An entity’s employee email account was compromised as a result of QR code phishing, also known as ‘quishing’. The employee was deceived into scanning a QR code that appeared genuine, which generated a token that allowed the threat actor to by-pass multi-factor authentication.
To prevent reoccurrence of similar incidents, the entity increased cyber security awareness training from once to twice a year and sent out staff communication about QR code phishing. The entity also engaged an IT provider to review whether its email platform could block QR code phishing attempts in the future.
The OAIC outlined some reasonable steps entities can take to precent a data breach including:
- prioritising training staff on secure information handling practices
- holding regular training to keep staff up to date on the latest techniques used by threat actors and methods to detect phishing attempts
- minimising access to personal information to staff who require access to enable the entity to carry out its functions and activities
- proactive monitoring to identify possible unauthorised access by internal and external parties.
The OAIC also encourages organisations to:
- implement multi-factor authentication for access to business systems, online services and data repositories, and for users when they perform a privileged action (using phishing-resistant multi-factor authentication will provide entities additional security that is not as susceptible to sophisticated cyber attacks)
- where multi-factor authentication is not available, enforce password management policies such as password complexity requirements or the use of strong passphrases, and ensure passwords are not being reused across systems
- layer security controls to avoid a single point of failure
- ensure users have appropriate levels of access to information assets depending on their role and responsibilities; monitor and regularly review accounts with more access permissions, removing access privileges where no longer required
- implement robust security monitoring processes and procedures to detect, respond to and report incidents, or unusual or suspicious activity, in a timely manner.
FortiTech has worked with a number of businesses to secure their data in the fight against cyber crime and for compliance requirements, we utilise a multi-prong approach including staff education, data security, firewalls and multi-factor authentication. If you want to ensure your data is safe and avoid the potential headache of a data breach then give us a call on 1300 778 078 or email to find out how we can help fortify your technology.