This weeks blog is a report written in response to a cyber incident involving a Brisbane Law firm who found themselves caught up in a scam centered around unauthorised access to the Microsoft 365 account of the firms Office Manager, Susie and the subsequent activity undertaken under the account by the unauthorized party. The names used in this blog are fictitious for privacy reasons.
Our blog provides a summary of the incident, remediation steps undertaken, an outline of the firms existing technology landscape
and post-incident recommendations. It also highlights the importance of Security
Awareness Training and strong cyber security practices are for your business.
Incident Summary
Susie called the FortiTech support line at 4.43pm on a Friday in September. During the call Susie advised that a client of the firm had received an email from her with incorrect bank account details for a property settlement. Susie confirmed that she did not send the email to the client.
At this point the issue was treated as a security breach and upon notification immediate steps were undertaken to ensure the renewed security of the firms electronic information. Once this was completed a more detailed investigation into the incident and any potential compromise within the firm was conducted.
Existing Technology Landscape
The Firms existing technology landscape is outlined below:
| Item |
Notes |
| Computers |
All computers are Microsoft Windows based and have password locks implemented. |
| Email |
Email services are provisioned through their Microsoft 365 tenancy |
| File storage |
There is no onsite file server in place. Client files are stored in cloud based software such as Microsoft SharePoint, TriConvey and LEAP |
| Email antispam |
All emails to @XYZBNElegal.com.au email addresses pass through a cloud based spam filter |
| Complex passwords for Microsoft |
Complex passwords are in place for Microsoft 365 accounts. |
| Multifactor Authentication |
Multifactor Authentication is active across all Microsoft 365 accounts |
| Microsoft 365 backups |
Daily backups of email are conducted Daily backups of SharePoint libraries are conducted |
| EndPoint Detection and Response |
EndPoint Detection and Response Enterprise edition is installed across all XYZBNE Legal devices. |
| DMARC and DKIM records |
DMARC and DKIM records are active on the XYZBNE Legal domain to authenticate legitimate emails sent by staff. |
| External email disclaimer |
An external email banner is in place on XYZBNE Legal Microsoft 365 Exchange. This is in the form of a coloured banner at the top of each external email noting to staff that the sender of the email has an external email address. This is of particular use in identifying external parties purporting to be internal through spoofing display names or email addresses. |
| Staff education sessions |
Staff undertake annual Staff Security Awareness Training sessions. |
Incident Response
Immediate actions undertaken
| Action |
Finding/Result |
|
Logged Susie out of all Microsoft 365 current sessions |
Log outs successfully completed for Susie’s account |
|
Reset Susie’s Microsoft 365 password to temporary password |
Susie’s password was reset successfully |
| Reset Multifactor Authentication for Microsoft 365 |
Multifactor Authentication was reset and enforced for Susie. Note that MFA was already enforced on Susie’s account prior to the incident. |
|
Scanned local computers for suspicious or unwanted programs or files |
Full Enterprise EndPoint Detection and Response scan undertaken on both of Susie’s devices. |
Subsequent actions undertaken
| Action |
Finding/Result |
|
Conduct a one-off check of lost credentials |
Check conducted for [email protected] email address in databases for lost credentials. No lost credentials reported. |
| Review sign in logs for all accounts to identify any suspicious activity |
Suspicious sign in activity was found on Susie’s Microsoft 365 account, being a single login from North Dakota, USA and multiple
subsequent logins from Virginia, USA. 16 September 2024 was the first successful login by the threat actors. This login took place in Minot, North Dakota, and was just over 1 minute after Susie had logged into Outlook on her laptop and likely clicked on a link or opened a malicious email attachment. |
| Review Susie’s emails for suspicious deleted or sent items |
At least 2 emails did not match legitimate sent items and a number of emails were found in the deleted items folder of Susie’s mailbox
that were either sent or received and then deleted by the threat actors. |
|
Check auto forwards on email accounts |
No suspicious auto-forwards were found to be in place on the XYZBNE Legal's Microsoft 365 tenancy. |
| Check of all exchange rules |
All Exchange Rules were checked and confirmed to be legitimate. |
| Check rules on Susie’s email accounts |
Susie’s Outlook was checked for any mailbox rules, 2 separate rules had been set up to filter emails from [email protected],
[email protected] and any emails from the apollo.io domain. The likely purpose of the rules was to subvert any replies from the above
addresses from being seen by Susie as the [email protected], [email protected] email addresses related to the client who had received the
fake email. The email contained incorrect information about the settlement. |
|
Check spam filters |
Cloudbased spam filters checked and confirmed no suspicious activity. Alerts were seen in Microsoft 365 for phishing attempts, however these alerts were deleted by the threat actors before they could be seen by Susie. |
|
Check Multifactor Authentication devices associated with Susie’s account. |
The multifactor devices associated with Susie’s account were checked to confirm they were all legitimate, during this check, it was
discovered that an iPhone 12 device had been added by the threat actors , had Susie’s password not been changed and the iPhone 12 MFA
removed this could have allowed the threat actors to again access Susie’s account at will. |
|
Check of internet history |
Both Susie’s PC and Laptop were examined in an attempt to locate the email or website that was utilised to garner the session token used
to access her account. As the initial login undertaken by the threat actors indicated it was a session token assigned to Susie’s laptop, the search focused on the laptop, however no history was found on either internet browser that Susie had installed. |
| Change Microsoft 365 tenancy to include Conditional access to AU only |
XYZBNE Legal Microsoft 365 tenancy was locked do to only allow access from Australian based connections. |
|
Investigation of an impersonation domain |
After Susie’s account was secured and the threat actors no longer had access, a XYZBNE Legal client received an email from the threat
actors. The threat actors were utilising an impersonation domain XYZBNElegalservcies.com (misspelling included) to create and send emails under the guise of being Susie. The emails also copied in the legitimate email addresses of XYZBNE Legal Services staff and therefore filtered through the antispam portal. The impersonation domain was found to have been created on the day access was cut for the threat actors and the domain was reported to the domain registrar and subsequently shut down the next day. |
| Continued checking of attempted login |
FortiTech actively monitored any further suspicious sign in attempts on Susie’s account after and found a further unsuccessful attempt on 21 September 2024, again from Virginia USA. |
Report Conclusion
The source of the security breach was found to be a phishing email which Susie opened on her computer, upon Susie either clicking on an email link or opening an attachment the email which upon activation opened a web browser and copied a session token, sending that token back to the threat actors who just over a minute later utilised that token to access Susie’s account from North Dakota. The history of that action was then wiped from Susie’s browser.
As there were a number of emails in both Susie’s inbox and the numerous mailboxes Susie has access to around about this date and time it is hard to pinpoint the exact email that was clicked on.
Upon being alerted to suspicious emails by a client Susie undertook the correct steps to report the issue to FortiTech for investigation and remediation as soon as she became aware.
Our investigation indicates that the threat actors went to great lengths to ensure their access to Susie’s Microsoft 365 account to undertake their criminal activities with the goal of illegally securing funds from XYZBNE Legal clients.
These lengths included, but were not limited to:
- adding an iPhone device for Multifactor Authentication under Susie’s account
- Once their access was cut, they went to the extent of creating a fake domain with a very similar name to the genuine XYZBNE Legal one when they no longer had access under the Session Token login and then proceeded to email other clients seeking payment of funds
- The continued to attempt to access Susie’s account after the initial access was cut.
As at the writing of this report no financial losses were experienced by XYZBNE Legal clients.
What is Session Token Theft?
Attackers steal tokens so they can impersonate you and access your data for as long as that stolen token lives. To do this, they get access to where a token is stored (on the client, in proxy servers, or in some cases in application or network logs) to acquire it and replay it from somewhere else.
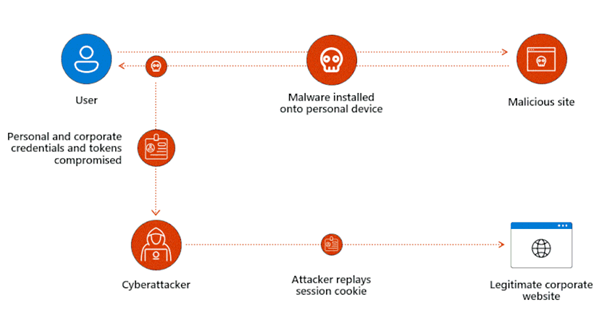
When an attacker steals your session token, it’s like picking your pocket after you’ve purchased your all-access season park pass at the fair’s ticket office. Because a token is digital, token theft is like stealing the pass from your pocket, making a photocopy, and then putting the original back in your pocket. The attacker can use their copy of your session token to get unlimited new access tokens to keep stealing your data, just as they can show a copy of a valid park pass to keep getting on rides without paying.
An attacker stealing your access token is comparable to someone stealing your ride ticket as you stand in line. They do the same copy-and-replace trick, using their copy of your token to access the resource, just as they could show a copy of a valid ticket to get on an individual ride without paying.
And because in both cases the attacker puts the original pass or ticket back in your pocket, you don’t even know an attacker is riding the rides in your name. Your token seems fine, even though an attacker is using an illegitimate copy of it, and it may take a while to determine that anything is amiss—if you ever do.
In this instance, the session token for Microsoft 365 was taken and used to access Susie’s account.
After a stressful time for the XYZBNE Legal team we are pleased to report no further instances of a cyber threat have occurred.
Our Latest News & Blogs

Pinch Payments: The Easy Way to Automate Payments in Xero, MYOB & QuickBooks
Tired of chasing late payments? Pinch Payments automates invoice payments in Xero, MYOB, and QuickBooks. Get paid faster with secure, PCI-DSS compliant transactions. Find out more about this Brisbane based business in our latest blog.