David Speaks: Cyber Security Awareness Training for Brisbane Transport company
This week David led a cyber security training session for the staff of a Brisbane based transport company.

Client Install: Migration from GoDaddy to Microsoft 365
GoDaddy is often a convenient starting point for small businesses due to its bundled offerings and simple setup. However, for growing businesses, GoDaddy’s version of Microsoft services quickly becomes restrictive. Find out how we helped a new law firm find their freedom, and security, in Microsoft 365 direct.

Tech Tips: Microsoft Bookings Advanced Features
Back in 2022, we introduced the basics of Microsoft Bookings—how to set up your calendar, add services and staff, and share your booking form. It has become one of our most popular blogs. In this follow-up, we’ll highlight some lesser-known but powerful features you can take advantage of. Whether you're looking to reduce no-shows, gather more customer info, or get better oversight of your bookings, there’s something in here for you.

The Importance of Having a Business Continuity and Disaster Recovery Plan for Your Business
We all know that unexpected disruptions—whether it’s a cyberattack, power outage, or even a natural disaster (thanks Alfred!) —can seriously impact business operations. But having a solid Business Continuity and Disaster Recovery Plan in place can make all the difference in keeping things running smoothly when challenges arise. To help, we’ve put together a free template to get your started.

Pinch Payments: The Easy Way to Automate Payments in Xero, MYOB & QuickBooks
Tired of chasing late payments? Pinch Payments automates invoice payments in Xero, MYOB, and QuickBooks. Get paid faster with secure, PCI-DSS compliant transactions. Find out more about this Brisbane based business in our latest blog.
Tech Tips: The Top 6 Features of Microsoft Edge
Is Microsoft Edge better than Google Chrome? Well, with these top 6 features, it definitely gives some food for thought. Dive into our latest blog to learn about 6 great features of Microsoft Edge that you could use in your business.
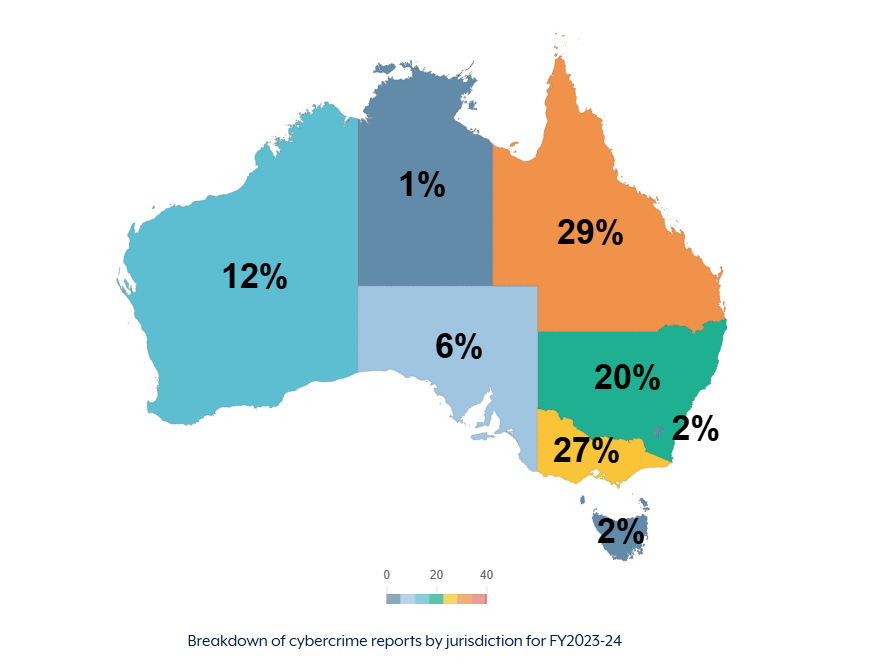
Queensland leads the nation in cyber crime
The Australian Cyber Threat Report for 2023–2024, released by the Australian Signals Directorate (ASD), highlights a significant escalation in cyber threats affecting businesses across the nation. Find out the key details in our blog.

Our top blog posts of 2024 revealed
We’re proud to share the top 5 blogs that have helped businesses stay informed and ahead of the curve in 2024.

Meowy Christmas from our Tech Sup'paw't team
As 2024 rolls to a close, our Paw-some foursome Tech Sup'pawt' team wish you a very Meowy Christmas with your friends and family.

Client Install: Roundup of our latest installs
It has been a busy lead up to the end of 2024 with a number of installations of new computers for our clients. We offer turnkey solutions for our clients and can deliver and install a new laptop or desktop PC in as little as 2 days. Find out about our latest installs in our blog.

Tech Tips: The best ways to use Google search
Google Search is an essential tool for businesses and professionals alike, but are you getting the most out of it? Whether you're looking for precise information, exploring industry trends, or hunting for market insights, mastering Google Search can save time and effort.
.png)
Cyber Security incident hits Brisbane Law Firm
This weeks blog is a report written in response to a cyber incident involving a Brisbane Law firm who found themselves caught up in a scam centered around unauthorised access to the Microsoft 365 account of the firms Office Manager, Susie and the subsequent activity undertaken
under the account by the unauthorised party.
Our blog provides a summary of the incident, remediation steps undertaken, an outline of the firms existing technology landscape
and post-incident recommendations. It also highlights the importance of Security
Awareness Training
and strong cyber security practices are for your business.
.png)
Defense in Depth Explained
For small and medium-sized businesses (SMBs), safeguarding sensitive information and ensuring uninterrupted operations requires a
proactive, layered approach to security. One highly effective strategy is Defense in Depth.
This blog will unpack the concept of Defense in Depth in simple terms, explain its benefits, and offer practical examples of how your
business can adopt this powerful cybersecurity framework.

How AI is Advancing Phishing Attacks – And How Your Business Can Stay Ahead
Phishing attacks have always been a major threat to businesses, but the game has changed. With the rise of Artificial Intelligence (AI), these scams are becoming more sophisticated and harder to detect, putting businesses and their employees at increased risk. In this blog, we’ll explore how AI is powering more effective phishing attempts, the risks involved, and actionable steps your business can take to combat these evolving threats.
Tech Tips: The 6 best features on Windows 11
Windows 11 brings a range of powerful tools and customization options that can boost productivity and streamline workflows, especially for business users. Read our latest blog as we explore some of Windows 11’s top tips and tricks.
Tech News: End of Support for Windows 10
After 14 October 2025, Microsoft will no longer provide free software updates from Windows Update, technical assistance, or security fixes for Windows 10. Find out your options for using Windows 10 (or not) in our latest blog.

Client Install: New Law firm full technology setup
When starting a business, ensuring a strong technology foundation can mean the difference between a smooth launch and future disruptions. One of our recent projects was for a startup law firm that wanted to get things right from the beginning. Find out what we did to help deliver a full suite of technology solutions to start them off on the right path.
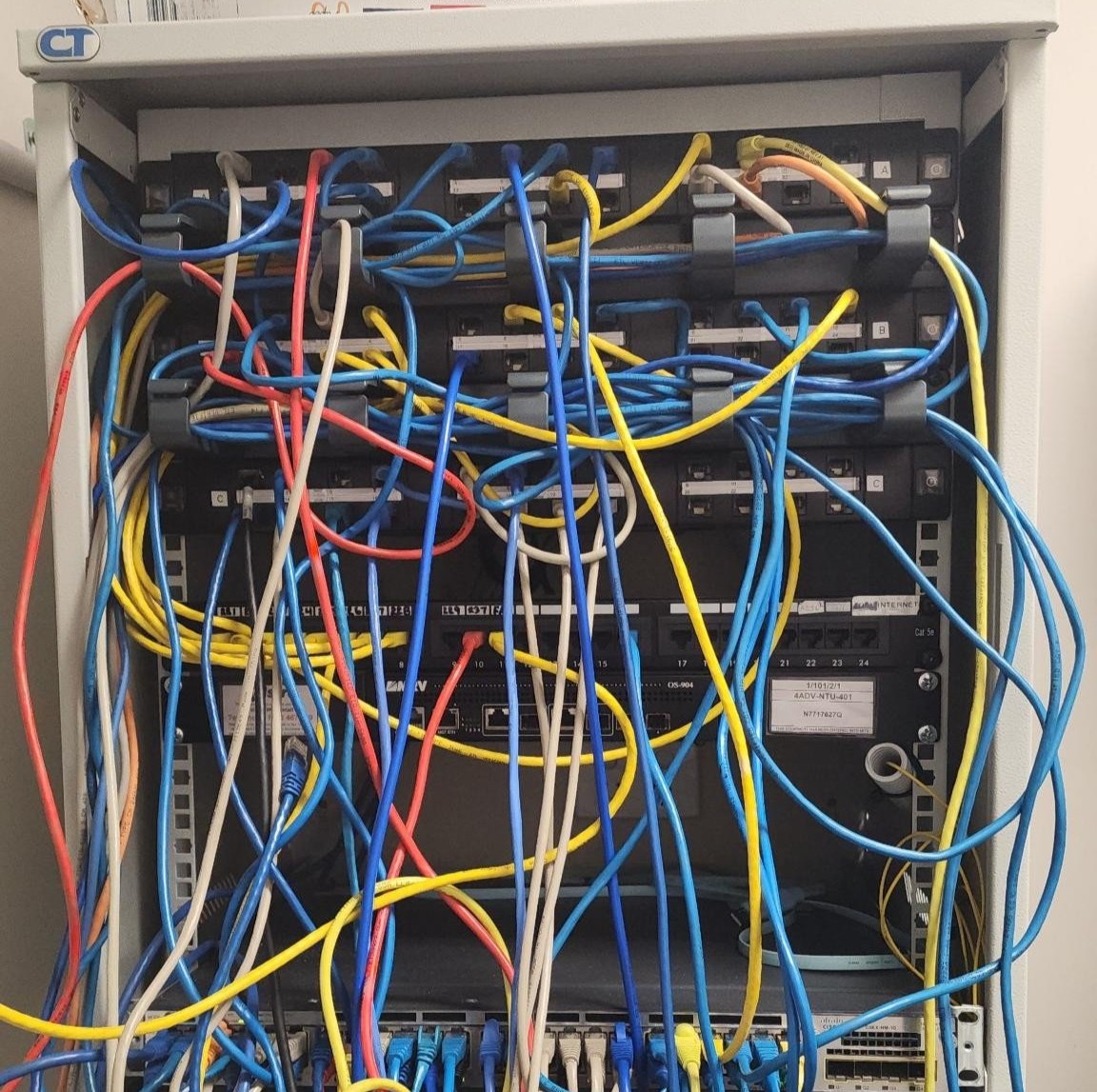
Network rack re-wiring and testing for a small business
We encountered a spaghetti junction of cabling when we attended the site of a new client this month. Find out how we turned their networking rack from a cabling disaster into an organised masterpiece in our latest blog.
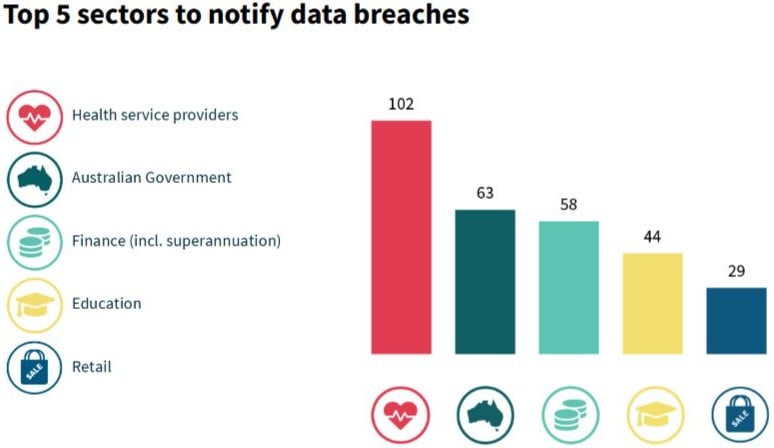
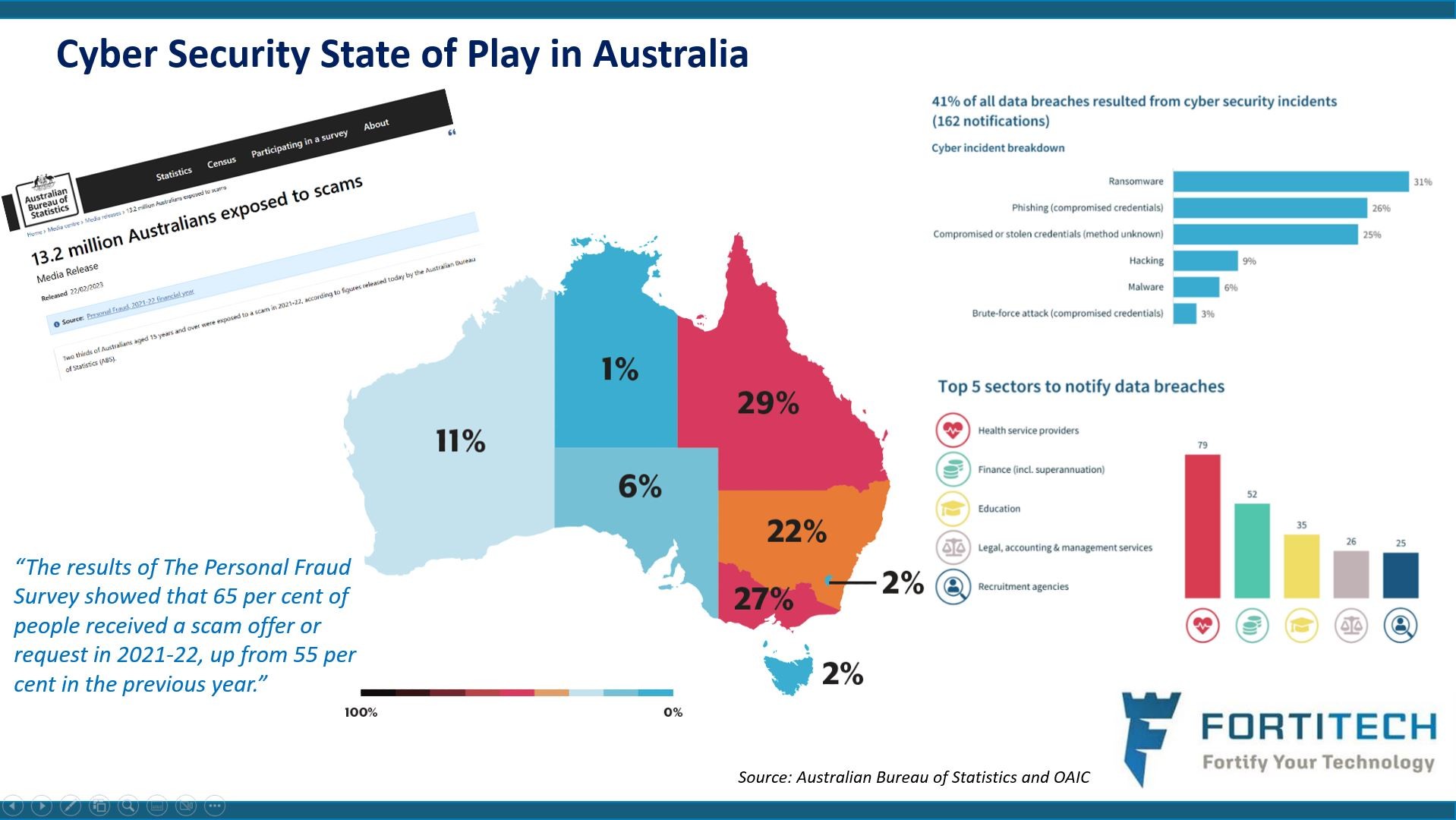
Cybersecurity news: The latest stats on Australian Data Breaches
October is cybersecurity awareness month which is great timing for the Office of the Australian Information Commissioner (OAIC) have released their Notifiable Data Breaches (NDB) Report for 1 January to 30 June 2024 and it makes for an interesting read.

We're certified geeks for Wi-Fi and Smart networks!
David achieves TP-Link Omada Certified Network Administrator (OCNA) Wireless Certification.

New retail store technology setup - network, CCTV & more!
One of our retail clients made the move to a bigger, brighter premises recently after outgrowing their previous space. This gave them the opportunity to set up technology at new store from scratch. Find out how we helped bring a dream to reality in our blog.

How often should a business replace their computers? Updated for 2024
How long should a business computer last? This is a question we are asked fairly often by our clients, especially when they are looking to purchase a new device. Technology is sometimes considered a large expense, but when that cost is spread over the lifetime of the device the annual cost can be quite reasonable. We delve into the ins and outs of the lifecycle of business technology in our latest blog.

Client install: 4 camera 4K CCTV system and NVR
The client's property was located on a corner block in a street experiencing ever increasing break-in's and general crime. Looking for peace of mind, they gave FortiTech a call to install a new CCTV system, find out what we installed in our latest blog.

Top Browser Extensions for Google Chrome
Scrolling through Chrome, extensions are the unsung heroes that can seriously boost your business efficiency. Let's dive into some of the top picks for Australian businesses looking to streamline their digital workflows!

Client Install: Line of Business software server for a retail client
This week we installed an onsite server for one of our retail clients. They are growing from strength to strength and are looking to
accelerate their sales and service even further through the use of some Line of Business software.
The specific software they have chosen requires a local server rather than a cloud based solution, whilst requiring an onsite server
for businesses is not as common as it once was thanks to more and more cloud based applications including Microsoft
365,
there are still instances like our clients' situation where it is required.

Tech Tips: Mail Merge in Microsoft Word: A Step-by-Step Guide to creating emails and letters
Microsoft Word's Mail Merge feature offers the ability to prepare both emails or letters, allowing you to create documents that are both
personalised and produced en masse. It is a simple and straightforward method to send communications out without the need for a third
party application or subscription.
In this guide we will walk you through how to create a mail merge document in Microsoft Word that you can them email through Outlook, or
simply print out and send.

Boost Your Business Efficiency: Top Browser Extensions for Microsoft Edge
Browser extensions can greatly enhance productivity and efficiency by adding functionality to web browsers, helping users automate tasks, manage passwords, and organise workflows more effectively. Read about some great browser extensions for Microsoft Edge that can help improve your day.

Client Install: 3CX VoIP Phone System for a Conveyancing firm
This week we went live with a new 3CX VoIP telephone system for a Brisbane based conveyancing firm. With a mix of handset and headsets and work from home integration, our client was thrilled with the result. Find out how we did it in our latest blog.

Client Install: Boosting Retail with Remote Desktop Server refresh
One of our long term retail clients reached out to us early last Saturday morning as their server had unexpectedly stopped working, as bad luck would have it , this occurred right before their business Saturday trading, so it was imperative to get things up and running again quickly for them as they utilised the server as a Remote Desktop (RDP) to run the Point of Sale (POS) system, which their 5 staff access. Read about how we helped them get back online in our latest blog.

Strengthen Your Business Defenses with Managed Detection and Response (MDR)
With cybercriminals constantly evolving their tactics, traditional antivirus solutions might not be enough to keep your valuable data safe. This is where Managed Detection and Response (MDR) comes into play, offering a proactive approach to cybersecurity that every business should consider.

Stop your emails being rejected by Microsoft 365 and Google
The increasing rise in digital threats has prompted Microsoft 365 and Google to introduce stricter authentication protocols. These protocols are not just about enhancing security—they're about protecting your business from the loss of customer trust and potential revenue. Find out how you can ensure your business emails meet these new requirements in our blog.

Tech Tips: Using Microsoft 365 Copilot
Copilot is all about enhancing productivity and creativity in your business tasks and best of all it is just a prompt away!
But how can you make the most of it? This blog has you covered, here are key insights to help you navigate and leverage Copilot’s
powerful features effectively.

Client Install: Server for a 10 user accounting practice
The challenge was clear: replace an outdated system with a robust, scalable solution designed for longevity, reliability and performance. Find out how we did it in our latest blog.

Tech Tips: Setting up Linktree for your business
Did you know that Linktree can be a powerful tool for businesses looking to streamline their online presence and direct traffic effectively? Essentially can be a central link to all of your social media profiles, website’s, even payment platforms. In this blog we will outline the key benefits and features of Linktree that can help increase your business exposure online and also provide a quick guide on how to setup a basic free profile, before you delve into the many paid options.

What is Microsoft Copilot?
The introduction of Microsoft 365 Copilot represents a watershed moment in workplace productivity. This groundbreaking tool, which harnesses the power of advanced artificial intelligence (think ChatGPT but on steroids), is set to redefine the way businesses operate, offering unprecedented levels of assistance in daily tasks and decision-making processes.

Client install: Remote Installation of 3CX VoIP Phone System for a Law Firm
Recently, our team had the opportunity to enhance the communication capabilities of a Queensland law firm. This progressive firm, with a team of 17 legal professionals, was looking to streamline their communication processes as part of an office move and wanted a flexible solution that also meant they weren't tied to one of the big telecomms providers. Find out how we helped them in our latest blog.

Tech Tips: Microsoft PowerPoint
Microsoft PowerPoint 365 is an indispensable tool in today’s digital world, used widely for creating engaging and informative presentations. This blog aims to provide you with a comprehensive set of tips, shortcuts, and insights to harness the full potential of PowerPoint 365. Get ready to transform your slides from mundane to magnificent!

David speaks: Cyber security awareness training
If you are one of our clients on our Maintenance and Security plans we provide you with 1 free cyber security awareness training session a year. This is exactly what happened for one of our longest held clients towards the end of 2023 when they arranged their annual session. Find out how it went in our latest blog.

Client Install: CodeTwo automatic email signatures for Microsoft 365
We recently implemented CodeTwo automatic email signatures for an accounting client on the Sunshine Coast just in time for their newly created signature to announce their holiday closure dates. Find out more about the project in our latest blog.

Our top blog posts of 2023
As we wave goodbye to 2023, it's time to reflect on the year gone by in the world of IT and cyber security. In this weeks blog, let's take a look at our top 5 most viewed blog posts of 2023.

Client Install: CCTV & Wi-Fi
This was a bit of a different CCTV & Wi-Fi install for one of our clients in the transport industry, they were looking to add more cameras and recording storage to an existing system and boost the Wi-Fi coverage out to their workshop. Typically, we would be called upon to install new CCTV systems from scratch, but our client wanted to stick with their existing system and expand its capabilities, which we were happy to accommodate. Find out what we did in our latest blog.

What is Wi-Fi 7 and is it worth the upgrade?
The upcoming release of Wi-Fi 7 promises a significant step forward in wireless communication. Especially for the business sector, where fast, reliable, and secure connections are non-negotiable.

Windows 12 is coming
No official announcement has been made, but it looks like the next version of Windows operating system, expected to be named Windows 12 is set to launch in the second quarter of 2024. Whilst we eagerly await Microsoft's official announcement we have put together our thoughts on what might be to come.

Tech Tips: Harnessing the Power of Microsoft To Do - Business Productivity Unleashed
Microsoft To Do is more than just a task management tool; it's a powerful ally in streamlining our workdays. Whether you're a seasoned user or just dipping your toes into its features, our guide promises insights that can transform the way you tackle your to-do list.
.svg.png)
Tech Tips: 5 ways to improve your workflow with Microsoft Outlook
Microsoft Outlook 365, a robust email and scheduling application that is widely used by businesses around the world. With its array of features, Outlook 365 can significantly streamline your workflow, making it easier to stay organised and get more done.

Cyber Security Awareness Training
For businesses, the risk of a cyber attack is ever present, given the vast amount of sensitive data they handle daily and that is exactly why one of our new clients went searching on Google for "Cyber Training Ipswich QLD" and ended up giving us a call.

David Speaks: Sunshine Coast AAT Discussion Group
David was invited to present a webinar this week for the Institute of Public Accountants (IPA) Sunshine Coast AAT Discussion Group for Bookkeepers.

What is Email Antispam and how can it help your business?
Are you a small business owner, constantly wrestling with a tidal wave of junk emails clogging up your inbox? You're not alone. Email spam has evolved into a major headache for businesses across Australia. But there's a solution: email antispam, find out what it is and how it can help your business in our latest blog.

Client Install: CCTV for a small business
Do you own a small business and need a reliable security system that keeps you connected to your workplace anytime, anywhere? We've just wrapped up an exciting CCTV installation project for a small business, read out latest blog to find out how it went.
David Speaks: IPA BAS Agent Discussion Group Webinar
Our very own Cybersecurity Advisor, David, had the privilege of presenting an enlightening webinar recently for the Institute of Public Accountants (IPA) AAT Brisbane and Gold Coast Discussion Group Meeting.

Tech Tips: The top 7 ways to boost your productivity with Microsoft Office 365
Get ready to kick those frustrating inefficiencies to the curb and unlock the full potential of your Microsoft 365 Office suite with our top seven productivity-boosting Tech Tips.

How we saved our client over $40,000 a year in phone and internet costs
In a recent success story, we helped a client save a staggering $40,000 annually (or over 50%!!!!) on their phone and internet bills. Find out how in our latest blog.

Client Install: Hikvision 11 Camera CCTV System
We recently completed the installation of a Hikvision 11 camera CCTV system on the northside, the system included storage for recording and AI functionality to recognise humans and vehicles. Find out how we did it in our latest blog.

Tech Tips: A guide to the best ways to use ChatGPT for small business
Looking to jump on the ChatGPT bandwagon? Here are some great tips and tricks to ensure you make the most out of using ChatGPT for your business.

Client Install: MSI Laptop with dock and dual screens for an Accounting Practice
In this weeks' blog we cover off the install of a new MSI laptop with docking station and dual monitors at an accounting practice.

David Speaks: IPA Ipswich chapter Cyber Security presentation
David makes a return visit to the IPA's Ipswich chapter to discuss the Anatomy of a Cyber Attack.

David Speaks: IPA 2023 QLD Conference
After a successful speaking engagement at the IPA National Conference on the Gold Coast in 2022, David was invited to speak again at the IPA QLD Conference at Noosa. Find out how it went in our latest blog.

Streamline Your Retail Business Network with TP-Link Omada and APC Solutions - An IT Support Business Case Study
Recently, we had the pleasure of working with a small retail business to upgrade their network setup, find out what we did in our latest blog

The top 7 reasons your business should use CodeTwo Automatic Email Signatures for Microsoft 365
CodeTwo email signatures for Microsoft 365 is a powerful tool that helps businesses to centralise and automate the management of email signatures. In this blog we round up the top 7 benefits of implementing it.

Our top 5 blogs in 2022
It was a close race between the top 2 most popular blogs of 2022, with only 1 view separating them, but 1 blog on a very hot topic reigned supreme. Find out what it was and the remainder of the top 5 in our look back on 2022.

ChatGPT: The Pro's and Con's of using it to market your business on social media
ChatGPT is all the rage at the moment, but what is it and how can it help (or hinder) your business marketing strategy?

Tech Tips: Getting started on 3CX
3CX is a powerful VoIP phone system for your business, with almost unlimited extensions and free calling to a number of destinations, it makes it a great choice for your team. In this blog we cover off setting up your 3CX extension for the first time on desktop and mobile devices.
